Authors: Arshit Jain and Sai Ahladini Tripathy, BeVigil Team
Editor: Isha Tripathi, Information & Analytics Squad
Widespread Exposure of API Keys Imperils the Mobile App Ecosystem
APIs have revolutionized how apps are developed and used. They make it easy for developers to build apps that communicate with multiple sources and efficiently manage data flowing to and from the apps. Hence, it is an integral part of how an app functions, hence app developers need to be cautious in how they handle these API keys and always follow secure coding practices to avoid any leak of their customer data and any systematic mishandling of API keys among app developers can cause a threat to the app’s business.
In the event of not following these practices, unauthorized access to the keys can allow threat actors to query sensitive information or access critical data. A North Carolina State University Research discovered that over 100,000 GitHub repositories had leaked API or cryptographic keys.
CloudSEK has observed that a wide range of companies — both large and small — that cater to millions of users have mobile apps with API keys that are hardcoded in the app packages. These keys could be easily discovered by malicious hackers or competitors who could use them to compromise user data and networks. In fact, multiple recent high-profile hacks, such as the Imperva breach, have leveraged this misconfiguration to compromise cloud infrastructure. Hence, hardcoded API keys are akin to locking your house but leaving the key in an envelope titled “do not open.”
Identifying Exposed API Keys of Payment Solution Companies
While the rampant exposure of API keys is hazardous for any app, it is especially critical when it comes to apps that handle payment information such as bank details, credit card information, and UPI transactions, in addition to user PII.
During our investigation, we found that out of the 13,000 apps currently uploaded to BeVigil, ~250 apps used the Razorpay API to enable financial transactions. And ~5% of these apps, i.e. 10 apps were found to be exposing their payment integration key ID and key secret. However, given that a purported 8 million businesses transact on Razorpay, the actual number of apps exposing API keys could be higher.
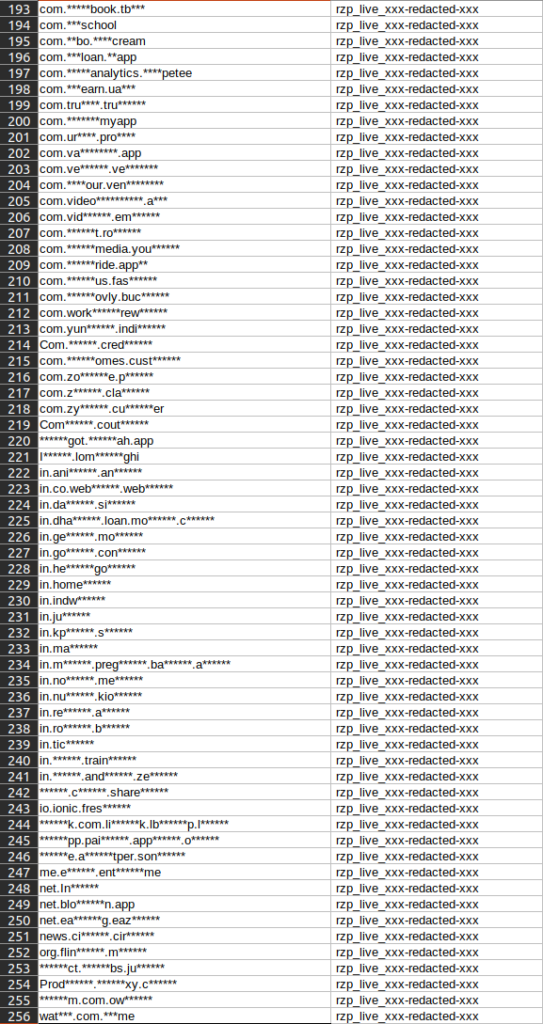
List of package names identified in Apps submitted to BeVigil having Razorpay payment integration.
This is especially concerning for the apps that process financial transactions by integrating with payment gateways.
This discovery comes on the heels of a similar finding that 100 million users’ data is impacted because 0.5% of mobile apps expose their internal AWS keys. This highlights a pattern of systemic mishandling of API keys among app developers.
When it comes to payment gateways, an API key is a combination of a key_id and a key_secret that are required to make any API request to the payment service provider. And as part of the integration process, developers accidentally embed the API key in their source code. While developers might be aware of exposing API keys in their mobile apps, they might not be aware of the true impact this has on their entire business ecosystem.
While this is not a flaw in Razorpay or other such services that provide integrations, it is evidence of how API keys are mishandled by app developers. So, it is up to individual companies to address the security concerns associated with payment gateways, AWS services, open firebases, etc.
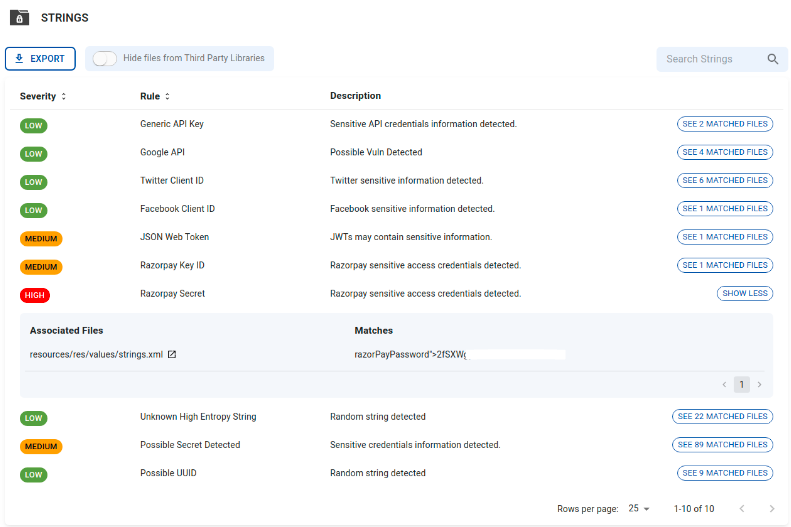
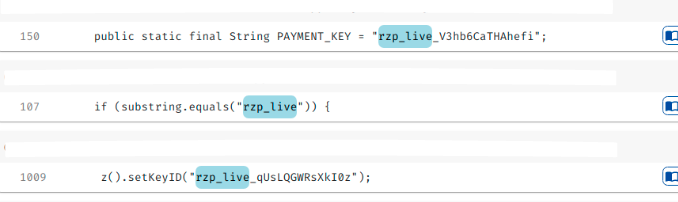
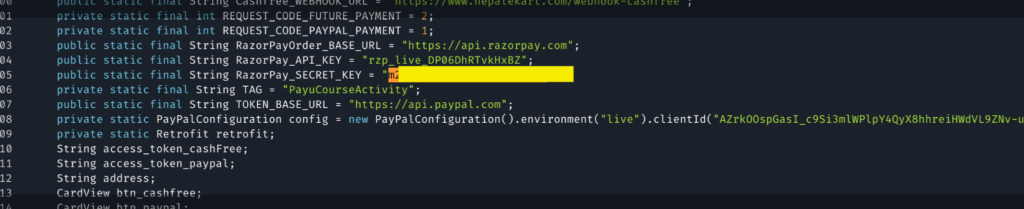
Sample evidence of an App containing the hardcoded API key_id and key_secret.
What is at Stake?
Using the exposed API keys threat actors can::
- Query Payment information
- Revoke unauthorized transactions
- Gain access to:
- User PII including phone numbers and email addresses
- Transaction ID
- Transaction amount
- Order details
- Refund details
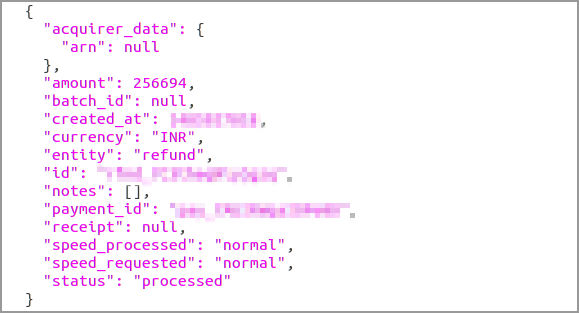
Data that can be accessed using the exposed API keys
- For most apps, payment providers are just one integration. They have integrations with other web apps and wallets, and also use on-premise services in offices, shops, etc. Hence, exposed API keys don’t just affect the app’s data, but the entire merchant organization’s payment data.
Once a threat actor has access to the above information, they can leverage it to:
- Initiate refunds using the compromised translation ID: An adversary can make bulk purchases and then initiate refunds. Such refunds can also lead to significant losses for the company. For example: In one of the apps we found a transaction for an amount of INR 1,82,813 along with the payment_id. And using just these two details an adversary could carry out a refund.*
- Sell user data on the dark web or to a competitor: A threat actor can either dump or sell the financial information, transaction details, user PII on cybercriminal forums and dark web marketplaces. They could also share the app’s consolidated data, proprietary research, and corporate financial records as competitor intelligence to other players in the sector.
- Orchestrate cyber threats: Threat actors can employ the users’ PII to carry out social engineering schemes, orchestrate scams, and even identity theft.
*Note: This possibility is based on the payment gateway documentation and we did not perform a PoC (Proof of Concept) for ethical reasons.


Order and Invoice details including amount, email, phone number
Extent of the Impact on Users and Businesses
The apps exposing API keys range from Health & Fitness to E-Commerce, and Travel & Hospitality to Healthcare & Pharma, many of which have over a million downloads.
Some of the major apps impacted include:
- One of India’s leading steel trading company
- Online grocery app
- Nepalekart (Instant Recharge to Nepal)**
- Top education app in south India
- Gold merchant
- Health App
**Note: The issue has been remediated and our security researchers were recipients of Bug Bounty awards for the disclosure of this incident.
| Category | Downloads*** |
| Health & Fitness | 1,000,000 + |
| Education | 10,000 + |
| Shopping | 50,000 + |
| Communication | 1,000,000 + |
| Shopping | 500,000 + |
***Note: The no of downloads as per play store for the Apps we found the hardcoded key-secret. Might not be directly related to the no of transactions via the payment integration.
Remediation
If your app is exposing payment integration keys or any other API keys, here are some simple steps to address the issue:
- 1: Invalidate the leaked key and regenerate a new key-secret pair.
- 2: Remove the hardcoded key-secret from the source code, and publish an update on the app store.
- 3: For Android applications, to regenerate API keys:
- Log into the payment gateway Dashboard
- From Menu select the mode for which you want to generate the API key
- Navigate to Settings → API Keys
- Click Regenerate Key
Challenges with Regenerating API Keys
While there is a remediation process, it could pose a new set of challenges because simply invalidating the payment integration key will stop the app from working and impact the organization’s business. In addition, the process detailed above could take multiple days to execute, depending on factors such as the number of downloads, the flexibility of distribution, etc. It could also be a challenge if the app is used in old versions of Android, since getting all users to update to the new version may prove difficult.
Hence, app developers will need to release a new version of the app with the key removed. In this new version, app developers need to make sure that they have built backend systems which can load the key securely and that the API key is not hardcoded. After releasing a new version of the app, the challenge is to force all of their users to migrate to the new version. Only after 100% of their users have migrated to the new version, will it be possible to revoke the key present in the old version.
Even if all users update their apps, the key would still be present in older versions of the app. While the older versions of the app may not be available on standard Android and Apple app stores, they can be present on third-party app stores. Even after 100% of the users have updated to the new version of the app, if the invalidated key is present in older versions of the app, the risk still remains. This is the part most developers tend to overlook.
In order to avoid these issues, app developers are encouraged to be cognizant of the long-term effects of exposed API keys and set up review processes to avoid exposing the keys in the first place.
The Way Forward
Given the complexities of regenerating API keys, payment providers should design APIs such that, even if the key has not been invalidated, there are options to minimise the permissions and access controls of a given key. And app developers should be given a mechanism to limit what can be done using a key at a granular level, like AWS does. AWS has put in place Identity and Access Management (IAM) policies that can be used to configure the permissions of every operation on an S3 bucket. This practice should be more widely adopted to minimize what threat actors can do with exposed API keys.
CloudSEK’s Responsible Disclosure
CloudSEK has responsibly disclosed these security concerns to the affected companies independently. However, 9**** out of 10 of the key secrets were active as on 13th Sept 2021 and the APKs are leaking the same. Unfortunately, even companies whose primary business is app-based haven’t fixed the issue yet.
****Note: As per Razorpay all of the 10 API keys has been deactivated as of 16th Sept’21
About BeVigil
BeVigil is the internet’s first and only security search engine for apps. CloudSEK’s BeVigil helps app users, cybersecurity researchers, app developers, and organizations to identify vulnerabilities in the source code, exposed/ hardcoded secret keys, and app permissions and mitigate the risks in a timely manner. To instantly get the risk score of any app visit https://bevigil.com/ or drop a note to [email protected].
About CloudSEK
CloudSEK is an AI-driven Digital Risk Management Enterprise. CloudSEK’s XVigil platform helps clients assess their security posture in real-time from the perspective of an attacker. XVigil scours thousands of sources (across the surface, deep and dark web), to detect cyber threats, data leaks, brand threats, identity thefts, etc. To learn more about how the CloudSEK XVigil platform can strengthen your external security posture and deliver value from Day 1, visit https://cloudsek.com/ or drop a note to [email protected].