What’s New 🚀✨
Security Report
You said, we did! BeVigil 2.0’s security report has changed both in terms of quantity and quality of relevant data for its users. With a brand-new UI, all the information you need is presented in a modern and intuitive dashboard!
Here’s what’s new in the security report:
Detect sensitive assets in the source code
BeVigil detects and notifies you to assets present in your mobile app source code such as cloud assets and sensitive IP addresses, all domains/subdomains. The top few assets we can detect are AWS buckets, Azure containers, Google cloud buckets, Firebase URLs, and much more.
Malware Detection
Remember InstaAgent, a chart-topping free app that was outed as malware after it was found that the app was harvesting Instagram usernames and passwords? Well, it’s not surprising, as the most common method hackers use to spread malware is through apps and downloads.
With BeVigil, you can detect if any app has malware present in it. We’re able to detect and notify you of the presence of Trojans, adware, and spyware.
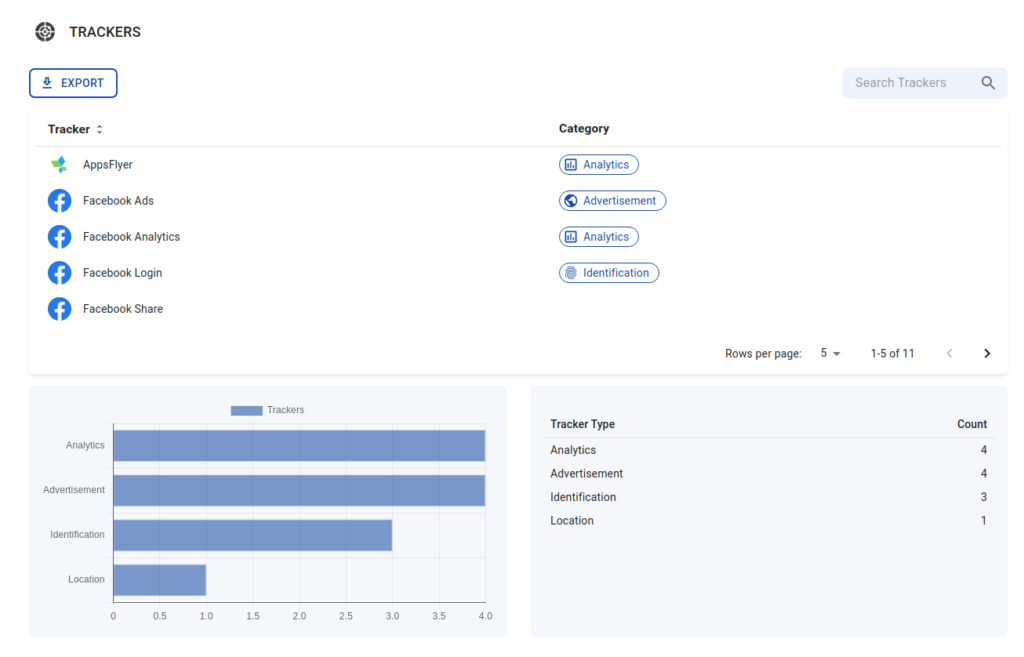
Find Trackers
Did you know that 75% of Android apps are secretly tracking their users? The trackers primarily gather location data, user habits, and other information to be used to target ads. In a largely unregulated space, there’s a fine line in between which can be often crossed by governments and large tech organizations. An example of the British government tracking people’s location to see if their behavior has changed after receiving the Covid vaccination proves this point.
BeVigil is able to detect trackers storing your personal information. Our capabilities include finding trackers in the following categories: Advertisements, Analytics, Crash reporting, Identification, Location and Profiling
APKiDs
APKiD analysis tells you what went into building an Android app. Android apps that are pirated or have malicious code injected are often decompiled and repackaged again with open source libraries such as dexlib. With such detection and fingerprinting of the building components of an app like the compiler, obfuscator, and packer, and presence of suspicious device information checks performed by the app, BeVigil users can detect pirated or malicious apps.
App Certificate
With the app certificate data in BeVigil, you can get details on the author of the app and also the signing scheme used. BeVigil users can now discern apps that are from a suspicious source with the certificate author details. For app developers, the risk they can mitigate with this data is the avoidance of using a deprecated signing scheme, using which even a legitimate app could get a malicious update.
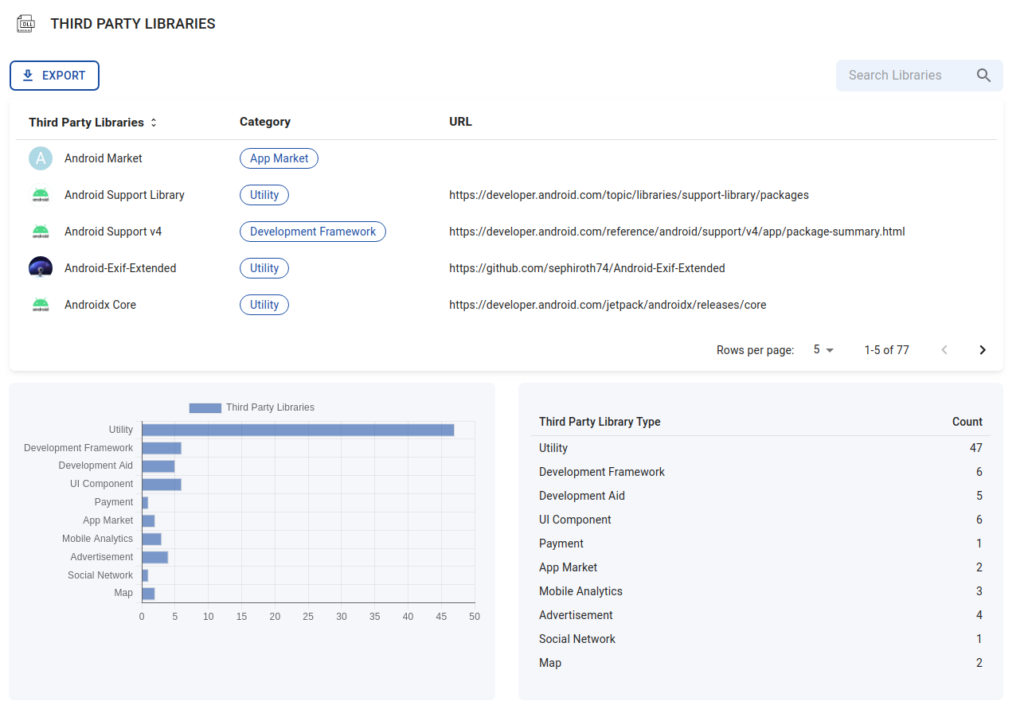
Third party libraries
With BeVigil, you can discover third-party libraries and services used in the app. As an app developer, you can discover vulnerabilities in third-party libraries used in your app, and make sure you have updated to the latest version.
Resiliency Requirements
Resiliency requirements are used to check if recommended measures for apps that process or give access to, sensitive data. Discover if these requirements, which increase your app’s resilience against reverse engineering and specific client-side attacks, are in place.
Enhanced Scan coverage
With BeVigil 2.0, developers can catch more vulnerabilities in the app, such as exposure of sensitive information in the app’s files and logs. BeVigil 2.0 now checks for twice as many sensitive keys and tokens of popular cloud, analytics, and authentication services in the app, and these hardcoded credentials are reported in the Strings section of the report. With the increased accuracy of the security scan in detecting vulnerabilities and leaks of credential information, BeVigil 2.0 gives app developers a better concise security report to act upon.
One For The Dark Mode Lovers 💪✨
Black mode
We couldn’t resist. The picture speaks for itself.
App Developers’ Round up  ✨
✨
Remediation Steps
BeVigil has moved in the direction of being a one-stop solution by providing severity, CWE, description and mitigation steps for each issue. App developers can deep dive into issues with capabilities to open, copy and share affected files with your team members.
Search Suggestions
BeVigil now offers you suggestions based on what you search for. Save time by directly going to app reports based on what BeVigil suggests!
Search within an app
Finally, search within your app for keys and hard-coded strings your developers generally use.
Scan your apps even faster
With drastic performance improvements, you can scan your app in less than a few minutes now.
Categories of trackers and third party libraries used
Get visibility into category-wise statistics of trackers and third-party libraries used in your app.
Choose to keep or remove matches from third party libraries
BeVigil gives you the option to hide files from third-party libraries making it convenient for you to view the most important results first.
In Conclusion
To sum it up, we hope BeVigil 2.0 provides value to app developers, security researchers, and organizations when securing their mobile apps. Our aim has always been to provide free tools for cybersecurity professionals and build a strong community to improve the security of the mobile app ecosystem.
If you have any ideas on what we should include in our next version, hit us up @ [email protected]
Until next time! 😃