With a market share of 72%, Android is the most widely used mobile operating system. The consistent increase in Android users has accelerated the development of apps considerably. Therefore, Android, with over 2.5 billion active users spanning over 190 countries, is a prime target for threat actors as well.
BeVigil is the world’s first security search engine for mobile apps. The analysis of more than 1 million Android apps indexed by BeVigil, allows us to identify the critical security issues that plague some of the most popular Android apps. One of the key issues involves apps requesting permissions that may not be necessary for their proper functioning.
In our previous blog, we explored what Android permissions are, how they can be (mis)used to orchestrate espionage campaigns and defraud users, and the dangerous permissions requested by popular apps.
In this blog, we show you how to identify if any app that you downloaded is requesting dangerous permissions. This is especially important because most people tend to accept all the permissions without knowing what exactly they are consenting to, how the information is being (mis)used, and what’s at stake. So much so that certain permissions can allow an app to compromise your privacy.
How Prevalent are Dangerous Permissions?
BeVigil shows that:
- 26% of educational apps access your microphone
- 21% of medical apps access your microphone
- 39% of finance apps access your camera
- 17% of finance apps have the read contact permission
- 46% of book apps have precise location access
Also read Dangerous Android Permissions To Look Out For In Your Apps
Does your App Ask for These Permissions?
Before you download any app, or if an app is already installed on your phone, check if it accesses your camera, contacts, or messages, even when it is not required for the app to function. Using BeVigil, you can do this in 3 simple steps.
Step 1: Select the App
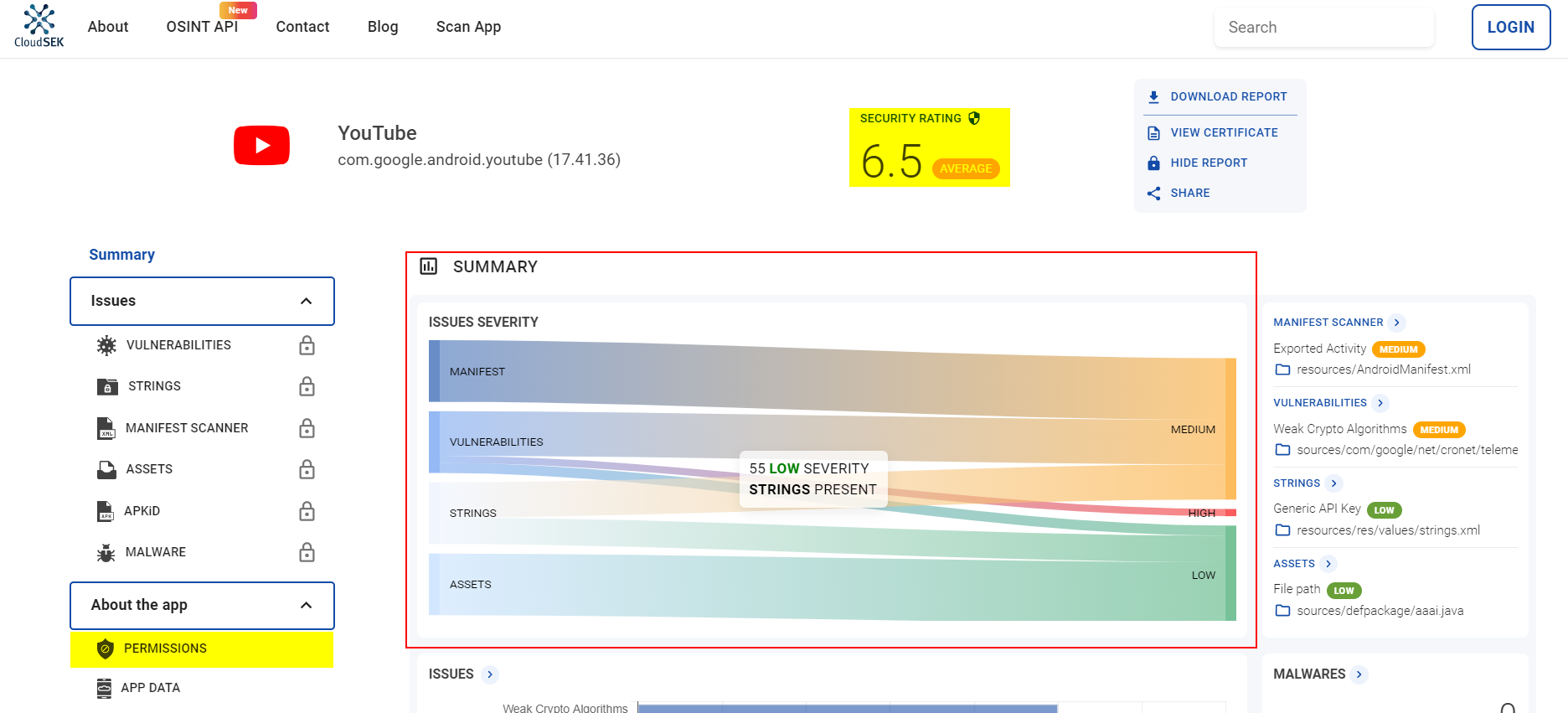
On https://bevigil.com/search, enter the app you want to scan into the search bar. Then select the relevant option from the dropdown menu. For example let’s select YouTube, which has over 10 billion downloads, to see what permissions it requests at the time of installation. (Figure 1)
Note: If the app you want to check is not listed on BeVigil, you can add the app’s App Store link at https://bevigil.com/scan-app. And in a few seconds, the app will be available for analysis. App developers can also upload their apps via this link to assess their app’s risk score.

Step 2: Check the security rating
The search will pull up a security analysis of the Youtube app, along with the overall security rating (or risk score). In YouTube’s case, the security rating is 6.5 (average) on a scale of 1 to 10, where 0 is the lowest score and 10 is the highest. On the same page, you can also get the issue summary of the app. (Figure 2)
Note: If you are an app developer, you should sign up for an account to explore additional features (it’s easy and free) such as what course of action can be taken to improve the security rating of your application.
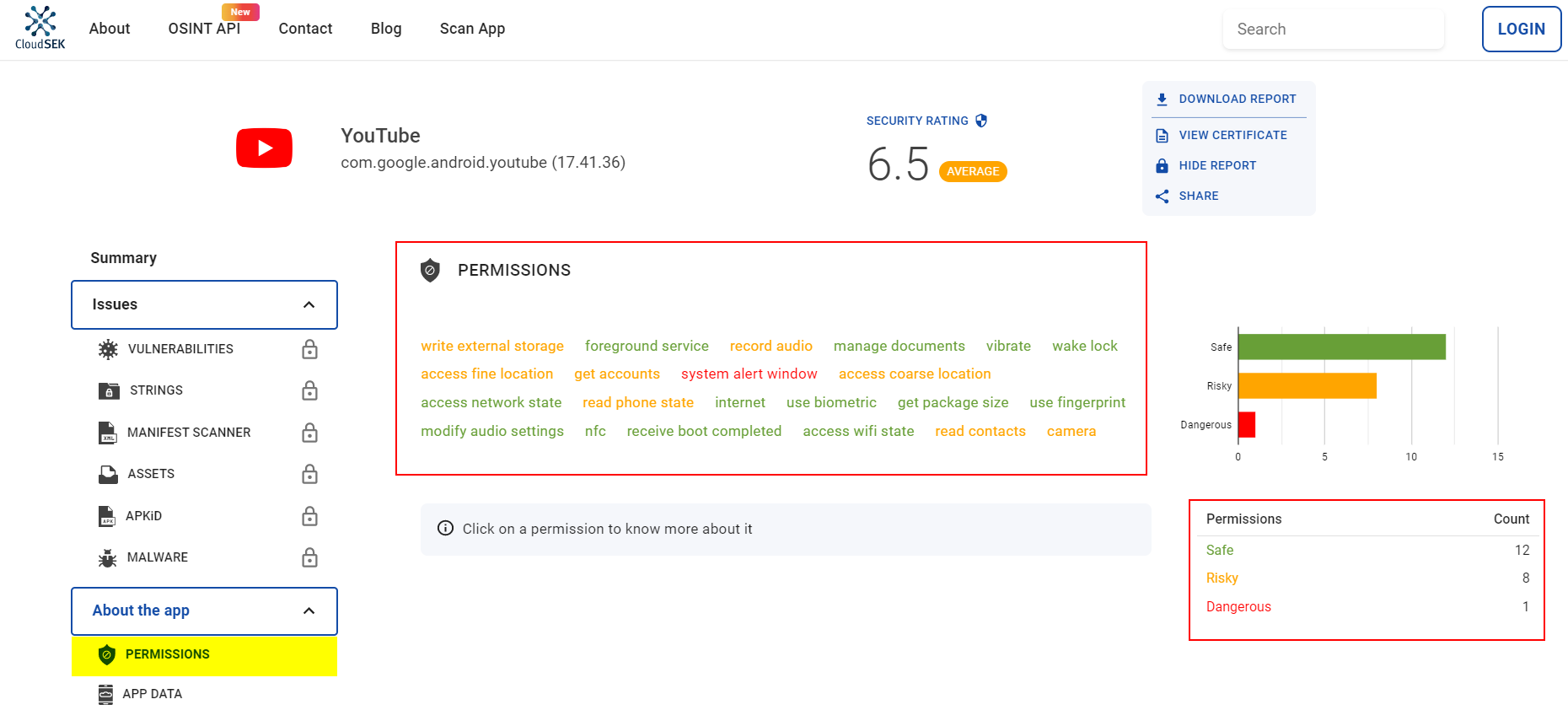
Step 3: Examine the permissions
Clicking on the Permissions button (on the left menu) will display all the permissions that the app requests. (Figure 3)
As we can see, there are 1 dangerous and 8 risky permissions that users give consent to during the app installation.
BeVigil indicates SYSTEM_ALERT_WINDOW as dangerous. This permission enables an app to display over any other app without notifying the user. According to a Check Point study, 74% of ransomware, 57% of adware, and 14% of banker malware abuse this permission as part of their operation. Threat actors misuse this permission to display fraudulent ads, phishing scams, click-jacking, and overlay windows, which are common with banking Trojans.
You can click on a permission to learn more about it (as shown in Figure 4).
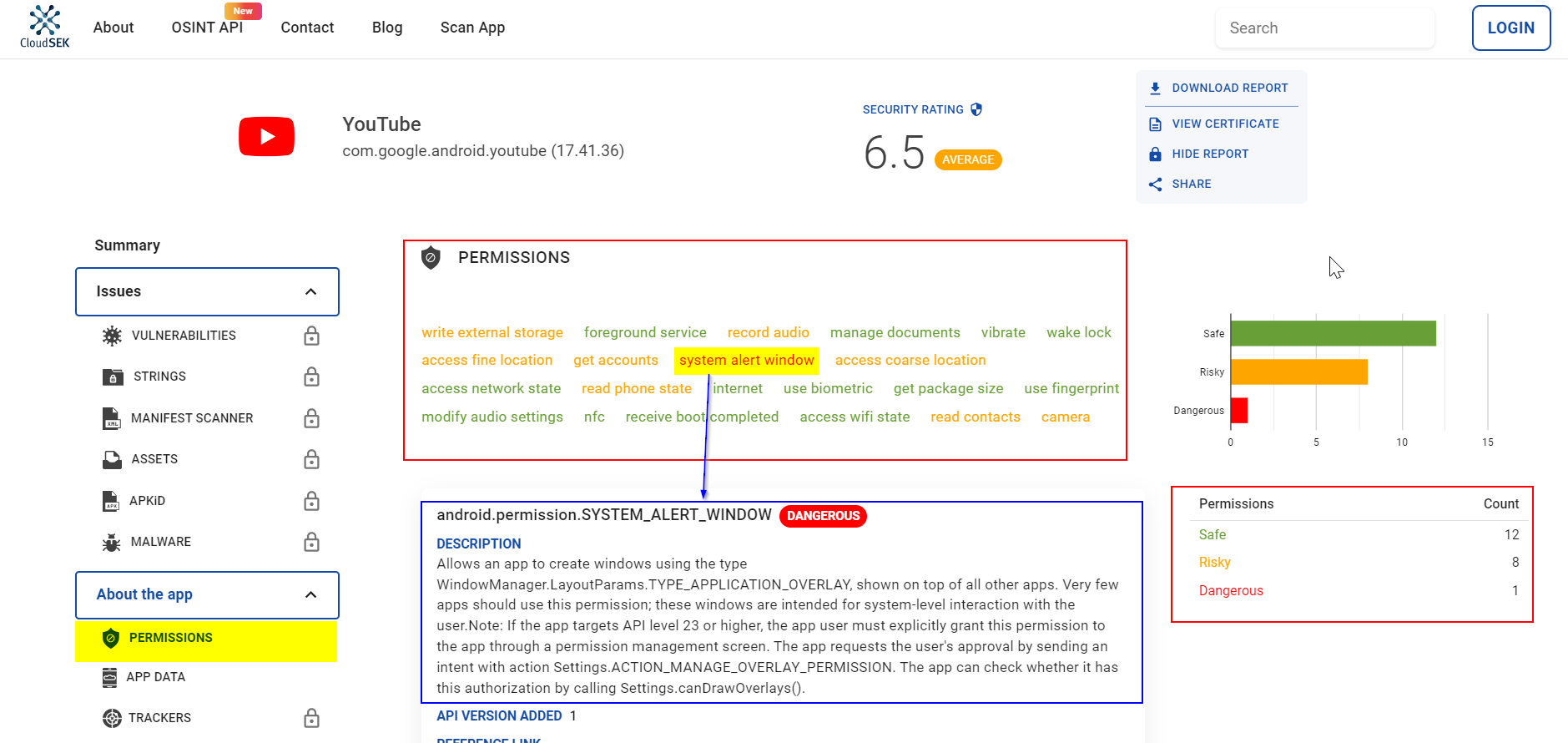
- ACCESS_FINE_LOCATION: Allows the app to access precise locations.
- READ_CONTACTS: Allows the app to read the user’s contact data.
- CAMERA: Allows the app to access the mobile camera.
While the app may have some legitimate use cases for these permissions, it is important for users to decide if they want the app to access their data and device functionality.
Auto-reset permissions from unused apps
Google recently introduced an auto-reset permissions feature with Android 11. So if you last used an app a few months ago, the permissions will automatically get reset.
As noted in the Android documentation (reproduced verbatim), “if your app targets Android 11 or higher and isn’t used for a few months, the system protects user data by automatically resetting the sensitive runtime permissions that the user had granted your app. This action has the same effect as if the user viewed a permission in system settings and changed your app’s access level to Deny.”
Conclusion
In this blog, we saw how to leverage BeVigil to assess the criticality of an Android app and make the right judgment before installing it. We also noted how dangerous permissions could change your system settings, modify your device password, lock your phone, or even permanently delete all the data from your device which could be disastrous.