Authors: Ashikka Gupta, Sudipta Pandit
Editor: Deepanjli Paulraj, Nithya Kurian
Android is the leading mobile operating system in the world with over 70% of all mobile devices worldwide running Android as of July 2021. You can download almost any kind of app from the Play Store, but before installing it, do you just select Accept to all permissions? Most people do. But what exactly are you consenting to? Certain permissions can allow an app, and the corporation that created it, to go as far as infringing on your privacy. To prevent companies from flagrantly accessing your private data, you must first understand what is at stake.
Apart from giving companies access to your data, apps with dangerous permissions are also used to disseminate malware, orchestrate espionage campaigns, and defraud individuals. In 2019, customers of several Czech banks reported money unexpectedly missing from their accounts. Investigators eventually traced it back to hackers who were employing malicious Android applications to overlay phony permission pop-up windows on top of real ones, to carry out unauthorized transactions to customers’ bank accounts.
What are Android Permissions?
An app usually comes with in-built features to do its job. However, there are still a number of permissions it needs to interact with you and your device. For example, a scanning app that needs access to your camera will request your permission to access your camera. This permission is known as CAMERA and is in most cases a safe permission to grant. However, it would be questionable for a calculator app to ask for this permission.
Be wary of Android apps that request permission to your device’s:
- Audio
- Location
- Contacts
- Camera
- Calendar
- Messages
- Biometrics
- Cloud storage (Read or Write access)
The Extent of the Problem
Analysis of over 148,000 apps indexed on BeVigil, the world’s first security search engine, showed that Educational apps, which account for 7.94% of the apps scanned, request for dangerous permissions more than any other category of apps. This is especially concerning, given that these apps are primarily used by children, who may not be able to discern the consequences of these permissions.
Of the permissions categorized as dangerous, the most commonly requested one was WRITE_EXTERNAL_STORAGE, with 64.45% of the total apps requesting it, followed by READ_EXTERNAL_STORAGE, which was requested by 50.67% of apps.
We also performed Permission Analysis For Android Malware Detection (PAMD) which is a method to evaluate the security level of Android applications based on their permissions by calculating the weighted averages. We found that 1564 of the totals app scanned had a Risk Score >0.5. Moreover, we also found that children’s gaming apps required a lot of unnecessary permissions like access to location, external storage, etc. Some apps with a high Risk Score and requiring strange permissions were: Temple Jungle Prince Run, City Construction Trucks Sim, and Fruit Link – Line Blast to name a few.
Some Dangerous Permissions To Look Out For!
- ACCEPT_HANDOVER
“Allows a calling app to carry on a conversation that began in another app.”
This permission enables a call to be routed to an app or service that you may not be aware of. If it switches you to a service that uses your data allowance instead of your mobile plan, this might cost you money. It might also be used to capture discussions in secret.
- ACCESS_BACKGROUND_LOCATION
“Allows a background program to access a user’s location.”
You must additionally request either ACCESS COARSE LOCATION or ACCESS FINE LOCATION when seeking this privilege. Simply requesting this permission does not provide you with location access. This permission, by itself, will not allow Google to monitor you, as Google claims. However, even if you believe you’ve stopped the app and it’s no longer tracking your position, it may still follow you.
- READ_CALENDAR
“Allows an application to read the user’s calendar data.”
The app would know where you’ll be and when. If you make notes with your appointments, it’ll also know why you’re there. Add location information, and the app will know how you got there too.
- READ_EXTERNAL_STORAGE/WRITE_EXTERNAL_STORAGE
“Allows a program to access external storage.”
If you grant the READ_EXTERNAL_STORAGE permission, any data storage that connects to your devices, such as a microSD card or even a laptop, might be accessed. The READ_EXTERNAL_STORAGE permission is implicitly given if you provide the WRITE_EXTERNAL_STORAGE permission. Using these permissions, the app can arbitrarily read/write data to any location on your device.
Analysis of Popular Apps on BeVigil
Now that we have realized how dangerous granting random permissions is, let us survey how widespread these are on the Playstore.
We analyzed popular apps on BeVigil: the world’s first security search engine, and here’s what we found.
A leading messaging app with 5B+ downloads:
Dangerous permission: REQUEST_INSTALL_PACKAGES
Impact: With this permission, the application can request to install external packages which may be harmful to your device.
Popular social media platforms with over 5B+ downloads:
Dangerous Permissions: SYSTEM_ALERT_WINDOW and BATTERY_STATS
Impact: BATTERY_STATS allows an application to collect battery usage statistics from your phone. This permission is a highly unnecessary permission to be required by a social media platform.
Mobile web browser with over 1B+ downloads:
Dangerous Permission: GET_ACCOUNTS_PRIVELEGED and WRITE_SETTINGS
Impact: GET_ACCOUNTS_PRIVELEGED which allows the app access to the list of accounts in the Accounts Service and WRITE_SETTINGS allows an application to read or write the system settings.
Emailing App with 1B+ downloads:
Dangerous Permissions: BIND_DEVICE_ADMIN and SYSTEM_ALERT_WINDOW
Impact: This app requests for the BIND_DEVICE_ADMIN permission which must be required by the device administration receiver, to ensure that only the system can interact with it. In Android, a screen overlay, often known as “Draw On Top,” allows one app to show content over another. This is made available by the Android app permission SYSTEM_ALERT_WINDOW. Because of its links to tap jacking assaults, this permission should be a source of concern to everyone. And, thanks to some Google adjustments, applications may now obtain that permission without the user’s awareness.
Using BeVigil To Find Dangerous Permissions
If you are ever unsure about permissions requested by an app, you can use BeVigil to ascertain the severity of permissions and then make an informed decision.
CloudSEK’s BeVigil is the world’s first security search engine that helps app users, cybersecurity researchers, app developers, and organizations identify vulnerabilities in the source code, exposed/ hardcoded secret keys, and app permissions mitigate the risks in a timely manner.
Just follow these simple steps to appraise an app:
Step1: Go to https://bevigil.com/search and type the name of any app, whose permissions you are curious about. As you start typing the name in the search bar, a dropdown will display the list of possible results.
Step 2: Once you select the app, you will be redirected to the app’s security report.
Step 3: On the left, you will see a Summary panel, click on the Permissions option under About the app.
The permissions required by the app are color-coded according to the level of severity. On the right, you can find a bar chart that shows the number of permissions categorized by their safety level.
Step 4: Click on any permission you want to find more information on.
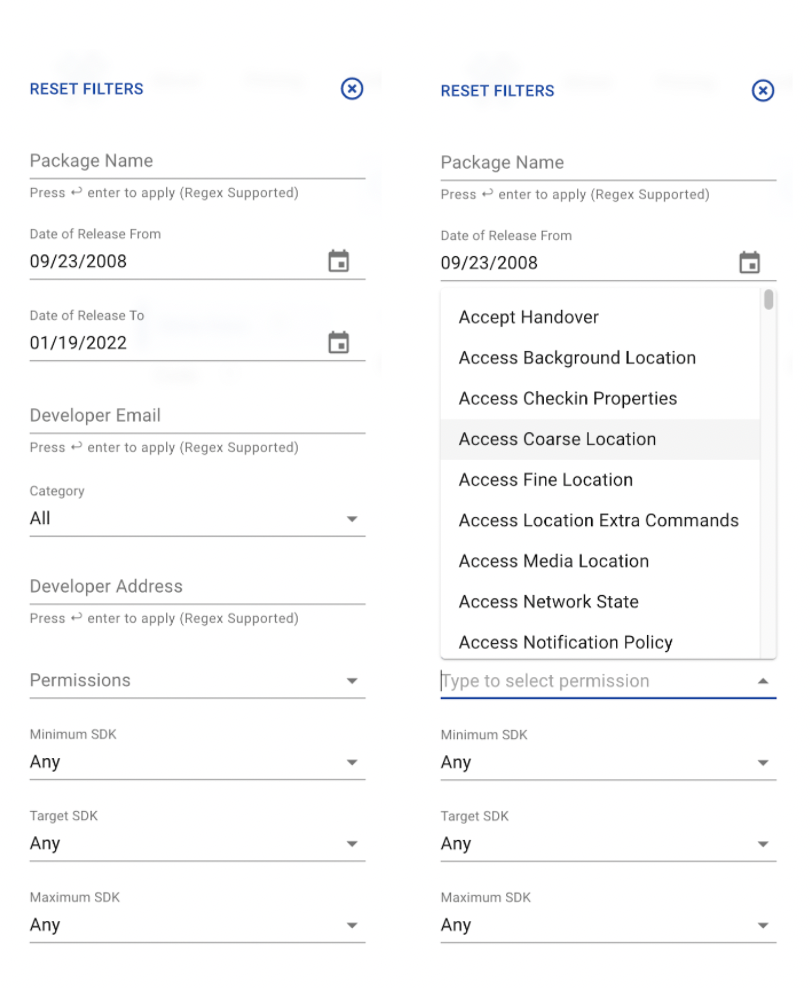
Also, by clicking the Additional Settings button, under the search bar, you will find many useful filters to enhance your search experience. One of them is the Permissions filter with which you can filter apps by specific permissions.
Protect Your Device And Yourself
Although many tech companies have started to acknowledge user privacy, Android permissions remain a grey area. This article covered only a small subset of the hundreds of permissions that modern Android apps utilize. Most users fail to understand the profound implications of these permissions.
As a user, the easiest way to protect your device and yourself from apps with these dangerous permissions is to be aware of all the permissions that an app requires. This way, you know exactly what you’re in for before downloading the app. A list of safe and dangerous permissions is available here.
There are nine categories of “dangerous” permissions on Android. Each of these risky permission groups has several permissions, and accepting one permission in a group automatically authorizes all of the other rights in that group. They are:
- Body sensors
- Calendar
- Camera
- Contacts
- GPS location
- Microphone
- Calling
- Texting
- Storage
Besides the permissions listed above, Android contains administrator privileges and root privileges, which are the most harmful category of permissions Apps with device administrator access can change your system settings, modify your device password, lock your phone, or even permanently delete all the data from your device. Any program with root access may do whatever it wants, regardless of which permissions you’ve banned or enabled previously.
There are, of course, going to be apps that genuinely require these permissions to function correctly. For example, it is reasonable for a fitness app to request the Body Sensors permissions and for a messaging app to request the Contacts permission. As a user, you must assess permissions based on the functionality of the app requesting them.
References
- https://www.inmobi.com/blog/2021/08/09/understanding-android-users-worldwide
- Giang, Pham & Duc, Nguyen & Vi, Pham. (2015). Permission Analysis for Android Malware Detection.
- https://www.avg.com/en/signal/guide-to-android-app-permissions-how-to-use-them-smartly
- https://www.online-tech-tips.com/smartphones/30-app-permissions-to-avoid-on-android
- https://in.pcmag.com/news/134176/android-malware-abuses-app-permissions-to-hijack-phones