Authors: Arshit Jain, Ashikka Gupta
Editors: Deepanjli Paulraj, Syed Shahrukh Ahmed
If you want to develop a steady and profitable business, you must have strong ties with your clientele. The process of honing these relationships, on the other hand, can be rather difficult. When it comes to engaging with your clients, having a Customer Relationship Management or CRM tool at your disposal can help you streamline and optimize your productivity. HubSpot is one of the leading CRM tools with over 128,000 users worldwide.
Over 1.6 million names, emails, and contact numbers are exposed by apps with hardcoded HubSpot API keys. HubSpot issues its users with API keys that developers utilize in their applications. Given the pace at which apps are developed and updated, developers often accidentally embed hardcoded API keys in their source code, making it easy for threat actors to obtain sensitive information.
This vulnerability was found using CloudSEK’s BeVigil, a security search engine that scans mobile apps and displays their security issues. BeVigil detected applications that serve millions of users, across sectors and regions, with hardcoded HubSpot API keys. Malicious hackers or competitors might quickly discover these keys and use them to compromise user data and networks.
CRMs and HubSpot
CRM is a tool used by organizations to help manage relationships with clientele. These tools collect data to provide more personalized interactions between the customers and the business. HubSpot’s CRM is used for marketing, sales, content management, and customer service. Most importantly, they deal with customer data, which is a valuable resource to hackers.
To enable these features HubSpot provides API keys to their customers to create applications or integrations. The keys are secret and can be misused to access an organization’s sensitive information. On scanning popular apps, BeVigil found 5 applications with hardcoded HubSpot API keys.
How Did We Find The HubSpot API Key?
Whenever a user submits an Android application for scanning, it gets indexed in the BeVigil search section. The search section contains all the popular apps that are submitted by users. Certain regexes help us find the secrets exposed in the indexed Android applications.
Our security research team used the HubSpot regex to identify apps that had hardcoded HubSpot API keys. This means developers embedded these keys in the source code, leaving them vulnerable to attackers. Information such as names, email addresses, and phone numbers was uncovered after the BeVigil scan. Unfortunately, this vulnerability is not uncommon; it is merely another instance of passive API security failure found by the BeVigil team (see our recent Razorpay disclosure).
What is the Impact?
Hardcoding API keys is negligent and risky. When attackers gain access to these keys they can obtain customer and app data. The following application was found to have hardcoded API keys:
| Application | Number of Downloads | Number of Users Affected |
| Popular Educative App | 50,000+ | 284 |
| Famous Productivity App | 10,000+ | 80,471 |
| Well-known Photography App | 50,000+ | 148,355 |
| Popular House & Home App | 10,000+ | 156,221 |
| Leading Education App | 500,000+ | 1,231,488 |
An endpoint could be used to fetch information of all the individual users as shown in the picture below.

The API key could also be used to extract PII of all the owners.
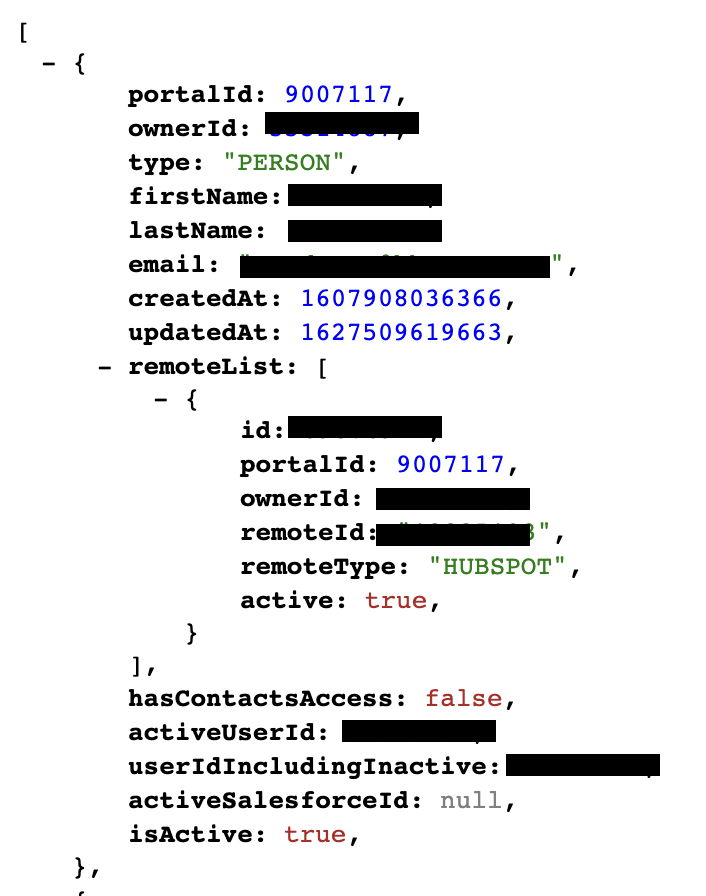
With the API Key, anyone can see all the information related to the application, such as contacts, files, workflows, pipelines, etc. An unauthorized user can also add new workflows, pipelines, blog posts, and send malicious marketing emails on behalf of the app.
Potential Consequences
Ill-intentioned hackers obtaining this kind of information spells bad news for the customers of the affected organization. Attackers can sell this information to spam or marketing callers. Competitors of these applications would also find this information valuable. This exposure is similar to what Thrillophilia experienced back in 2020. The misuse of their API keys led to sensitive data (names, usernames, location, and photos) of around 2 million users being exposed.
Companies that fail to protect their customers’ information, have to deal with the loss of trust and potential legal trouble. HubSpot would not be at fault as they only provide the keys. It’s up to the developers to keep those hidden. When a vulnerability like this is found, it is in the developer’s best interest to disable the key. The steps to disable an API key will be enumerated in the next section.
CWE 798 is the code assigned to vulnerabilities associated with hardcoded secrets and keys. You can search online security databases such as Open CVE to filter by this code and find security breaches.
Remediation Steps
A Hubspot API key can be deactivated by following these steps:
- In your HubSpot account, click the settings icon in the main navigation bar.
- In the left sidebar menu, navigate to Integrations > API key.
- Click the Actions dropdown menu, then select Rotate key.
- Click Rotate and expire this key now. Select the reCAPTCHA checkbox. Your existing key will be deactivated and a new API key will be created.
- Click Copy and replace the deactivated API key used by your applications with this new API key.
- Taking this security precaution can deter threat actors, but may create downtime for the application which can affect business.
How To Handle API Keys
The main takeaway from this article should be to not embed your API keys directly in your code. Listed below are actions developers can take to secure their keys.
- Standardized Review Procedures: The first step in hiding your key is to ensure correct versioning processes. Code pushes are frequently not subjected to a thorough examination. The codebase should be examined, reviewed, and approved for publication before versioning. Key exposure is less likely with standardized procedures. A good automated tool to check your quality code, application security and technical debt is sonarqube.
- Hiding Keys: Moving your keys outside of the source file structure is another smart way to disguise your keys. Instead, use a variable to refer to it. A variable in the environment makes it much easier to refer to the same key in different locations, saving time and enhancing security. Also, make sure you do not include the file containing environment variables in your source code. To know more about .env please refer to this blog.
- Rotate API keys: As a large proportion of hardcoded API keys are from old codebases, routinely rotating them helps mitigate the risk of leaked keys; unused keys are more unlikely to be invalidated to cause any real damage. Hubspot recommends rotating your API key every six months. This means a new key will be generated and the existing key will be deactivated. Vault is a tool for secrets management, encryption as a service, and privileged access management. It can help you manage secrets and protect sensitive data. Another such tool is AWS KMS which has a feature to automatically rotate keys every year.
- Security Keys and Secrets: Start hashing and encrypting your key, both in transit and at rest. This should add very little overhead to your interaction times if done correctly, but it ensures that any man-in-the-middle attacks or other breaches are difficult to leverage into larger losses.
- iPaaS: A cloud-based solution called Integration Platform as a Service is used for integration between applications and systems. This service is offered by several vendors, many of which include API management tools. This allows developers to monitor and control APIs in a safe environment. Vendors that HubSpot recommends can be found at this link.
- Obfuscate code or use an obfuscator: Obfuscating means modifying code so that it is unreadable for humans. This can be done manually or by using an obfuscator. This will keep the code functional but will make it hard to decipher if code is leaked.
Final Thoughts
Perhaps the best plan is to prepare for the worst-case situation. To begin, developers should use caution when implementing key limitations. Allowing only specific clients or components of the API to interact with a key reduces the damage the key might cause, and, as previously said, there’s no need for an omnibus key that’s used for a single function all the time. BeVigil can be used to scan for existing exposed keys and can be integrated with the development process flow to ensure continuous scanning
Another option is to link especially powerful keys to IP addresses or authentication mechanisms. Requiring a second factor before a call is authorized, connecting admin keys to admin IP addresses, and other measures can dramatically reduce key damage.
Finally, restricting the number of activities a key may perform on its own can be a significant deterrent to some assaults. Many flooding attacks are prevented by imposing a hard limit on what can be done in a short period of time, which can also be used to limit data exfiltration, abusive API usage, and concurrent connections.
References
- https://bevigil.com/blog/exposed-payment-integration-api-keys-imperil-millions-of-users-transaction-details-and-pii
- https://www.cnbctv18.com/travel/security-lapse-puts-data-of-thrillophilias-registered-users-at-risk-7252261.htm
- https://www.opencve.io/cve?cwe=CWE-798
- https://www.sonarqube.org
- https://platform.sh/blog/2021/we-need-to-talk-about-the-env
- https://www.vaultproject.io
- https://blog.hubspot.com/marketing/ipaas-vendors