Author: Bablu Kumar
Co-authors: Vishal Singh, Arshit Jain and Mayank Pandey
Introduction
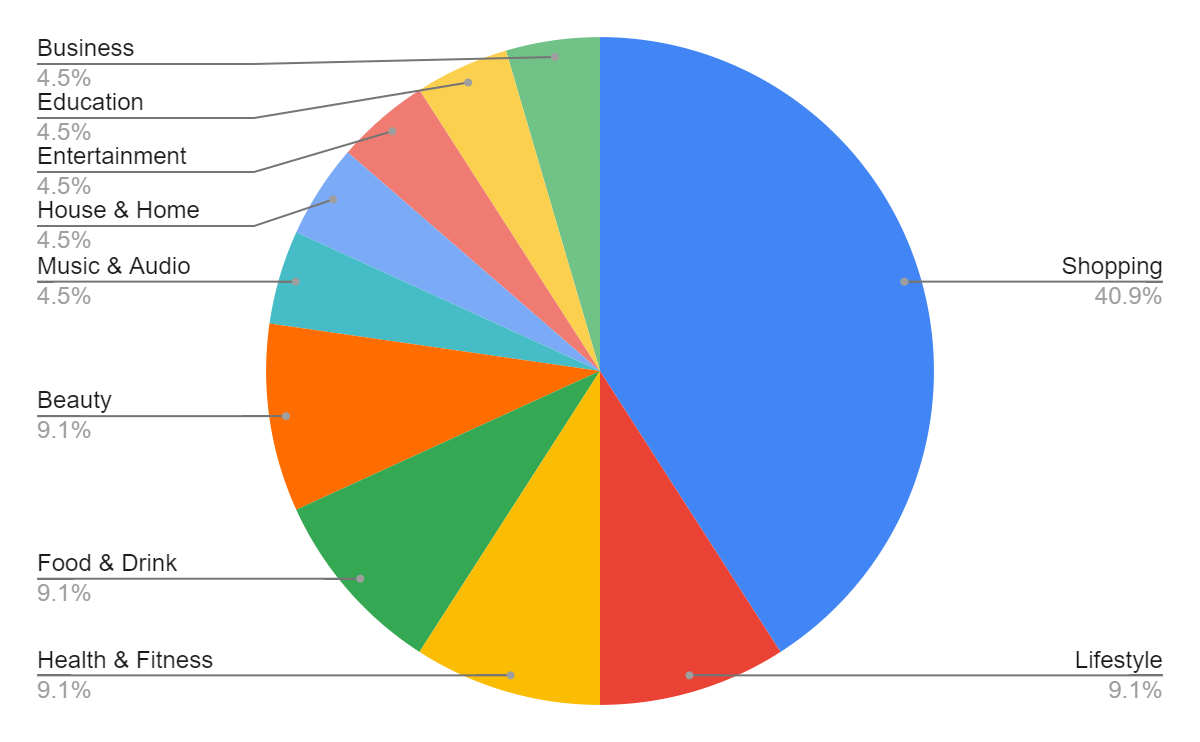
CloudSEK’s BeVigil, the world’s first security search engine for mobile apps, uncovered a critical security flaw in the mobile app industry. From the millions of Android apps indexed on BeVigil, 21 apps were identified to have 22 hardcoded Shopify API keys/tokens, exposing personally identifiable information (PII) to potential threats. These apps put close to 4 million users worldwide at risk, with shopping being the most affected category. Unfortunately, this vulnerability is not uncommon as this is another instance of passive API security found by the BeVigil team (see our recent coverage on email marketing API key leak putting 54 Million+ users at risk where we also highlight the secure coding best practices and Razorpay disclosure).

Shopify is an e-commerce platform that allows individuals and businesses to create an online store to sell their products. Over 4.4 million websites from more than 175 countries globally use Shopify as of 2023. With the ease of creating an online store, it also allows the integration of third-party apps and plugins to add additional functionality to the store. Shopify can be used to sell physical and digital products, and it also offers a point-of-sale system for brick-and-mortar stores.
Shopify provides several types of tokens that can be used for development. The type of token used depends on the specific development task and the level of access needed to the Shopify store data. We shall look at these tokens in particular:
- Shopify API Key: It is used to identify the app or integration that is making API calls. The API Key is generated when you create an app in the Shopify Partner Dashboard.
- Shopify Access Token: It is used to authenticate API requests. An Access Token is generated when a user authorizes an app to access their shop data. It is used to perform read-and-write operations on the shop’s resources such as products, customers, and orders.
- Shopify Private Access Token: It is similar to the Access Token, but it has higher privileges, allowing an app to perform sensitive operations such as creating and updating themes and fulfilling orders. The Private Access Token is generated in the Shopify Partner Dashboard and should be kept secure.
Note: While this situation is not a limitation of the Shopify platform, it highlights the issue of API keys/tokens being leaked by app developers.
Analysis of Hardcoded Shopify Tokens
Whenever a user submits an Android app for scanning, it gets indexed in the BeVigil search engine, along with all the popular apps submitted by other users. Our security research team used specialized Shopify Admin Key regexes to identify hardcoded secrets and tokens.
Interesting Findings from BeVigil
- 1,550 apps leaked Algolia API keys, out of which 32 apps contained hardcoded keys.
- 3,207 apps are leaking Twitter API keys that can be used to gain access/take over Twitter accounts.
- 0.5% of mobile apps expose AWS API keys, thereby risking their internal networks and data.
- 50% of the 600 analyzed apps were found to be leaking API keys of three well-known email service providers, Mailgun, MailChimp, and Sendgrid, putting over 54 million users at risk.
Note: For more such interesting findings, you can use CloudSEK’s BeVigil mobile application to assess these vulnerabilities of Android apps. Some of the salient features:
- Find security scores of more than 1 million apps
- Receive real-time notifications for new apps as to how safe they are
- Monitor and control critical permissions and more

Authentication
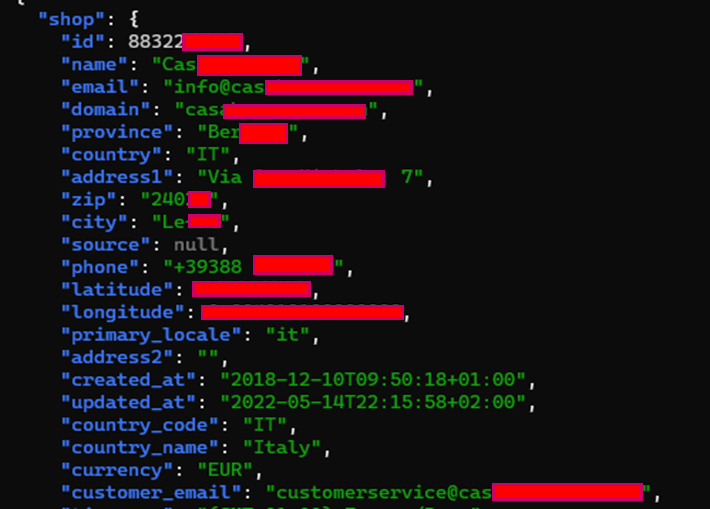
All REST Admin API queries require a valid Shopify access token. Using the hardcoded access token, threat actors can get shop details along with sensitive information such as the shop owner’s name, email ID, website name, country, complete address, phone number, etc. For the proof-of-concept, the researchers got shop details on authentication using one of the exposed API keys.
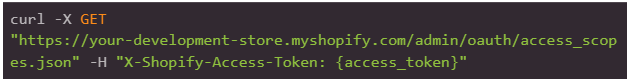
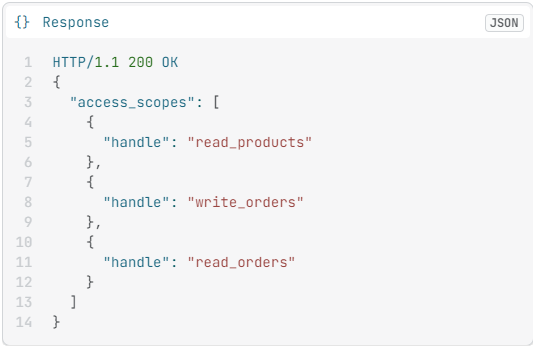
Access Scopes
The Access Scope resource allows you to retrieve the permissions that a merchant has granted to an app, such as read_orders and write_products. These permissions allow apps to access data from a shop, and are granted when a merchant installs the app or updates an existing installation of the app. Threat actors can orchestrate their attacks and exfiltrate data based on the granted permissions.
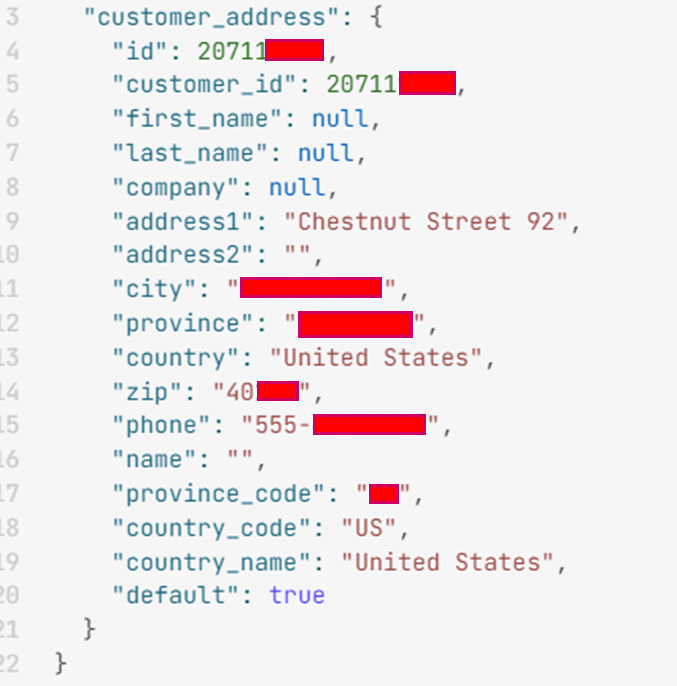
API Key Exposing Customer Data
The Customer resource stores valuable information regarding a shop’s customers, including their contact information, past orders, and email marketing preferences.
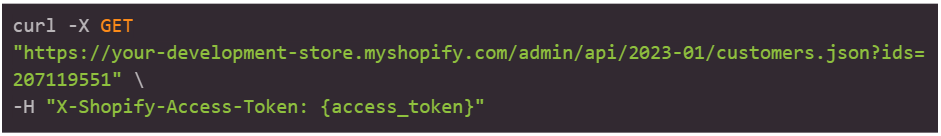
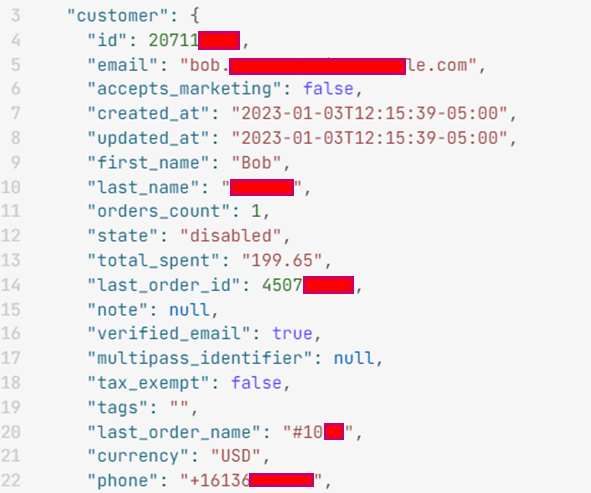
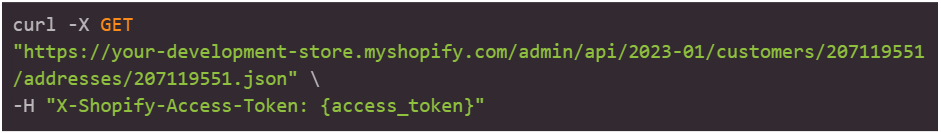
Furthermore, the API can also allow threat actors to view more detailed sensitive information about a particular customer ID.
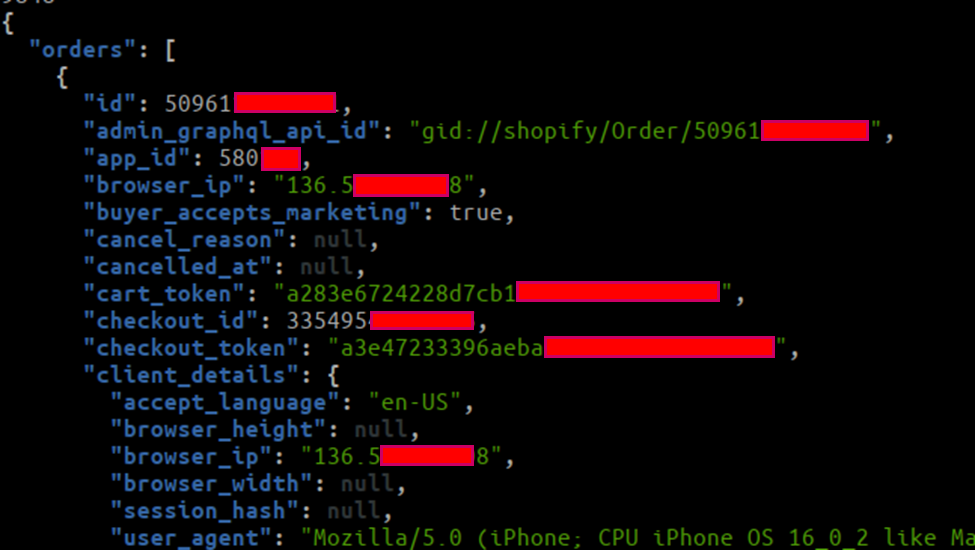
Exposing Order Details
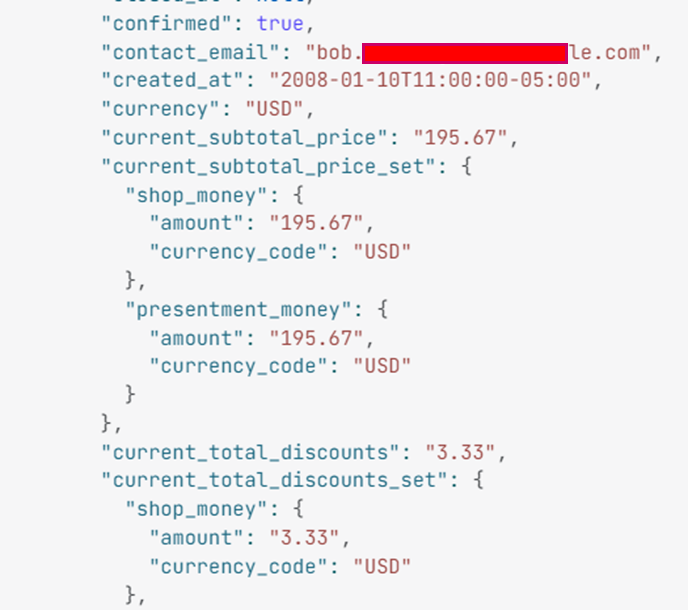
An order is a customer’s request to purchase one or more products from a shop. You can create, retrieve, update, and delete orders using the Order resource. The endpoint fetches the email ID, date, amount, etc.
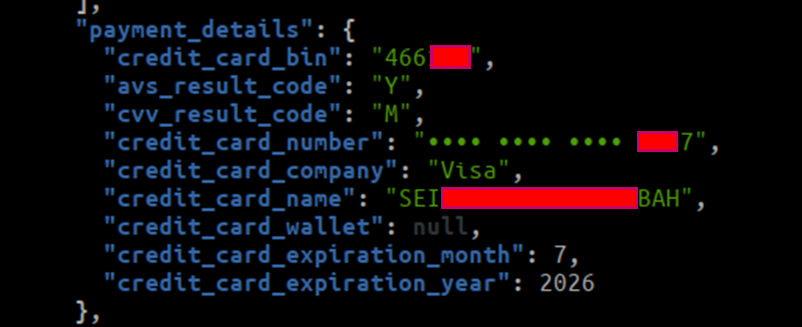
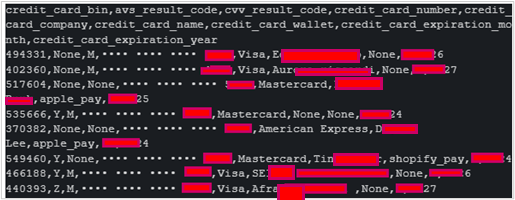
Exposing Card Details
Using this API endpoint, an actor with malicious intent could gain unauthorized access to banking transaction information such as credit/debit card details used by customers for purchases.
The compromised data include the BIN number, credit card ending number, credit card company, browser IP, name on the credit card, expiration month and year, etc.
Conclusion
The recent discovery of hardcoded Shopify keys in numerous Android apps is just another example of the lack of proper API security in the industry. This type of vulnerability exposes the personal information of users, as well as transactional and order details, to potential attackers. The impacts of these secret tokens are critical and not just limited to:
- Access to customers’ personal data that includes first name, last name, full address, phone number, country name, province name, city, province, email address, credit card details, etc.
- Access to write discounts that will allow an attacker to set a 100% discount on a product and in that case, the product would be almost free.
- Access to write price rules like creating a price rule that gives the buyer $100.00 off an order.
- Access to all the order details placed on that Shopify store.
- Access to create orders on Shopify Store.
References
- Hardcoded Algolia API Keys Could be Exploited by Threat Actors to Steal Millions of Users’ Data
- Mobile Apps Exposing AWS Keys Affect 100M+ Users’ Data
- Hardcoded API Keys of Email Marketing Services Puts 54M+ Mobile App Users at Risk
Appendix